R1#show run int gig1.12
Building configuration...
Current configuration : 95 bytes
!
interface GigabitEthernet1.12
encapsulation dot1Q 12
ip address 1.1.1.1 255.255.255.0
end
R2#show run int gig1.12
Building configuration...
Current configuration : 95 bytes
!
interface GigabitEthernet1.12
encapsulation dot1Q 12
ip address 1.1.1.2 255.255.255.0
end
R1#ping 1.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms
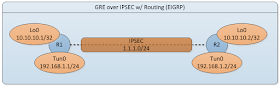
Now let's configure the Generic Routing Encapsulation (GRE) tunnel on both routers.
R1#sh run int tun0
Building configuration...
Current configuration : 139 bytes
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
ip mtu 1400
tunnel source GigabitEthernet1.12
tunnel destination 1.1.1.2
end
R2#sh run int tun0
Building configuration...
Current configuration : 139 bytes
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
ip mtu 1400
tunnel source GigabitEthernet1.12
tunnel destination 1.1.1.1
end
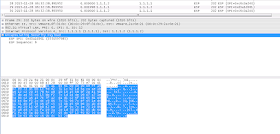
Notice that I am setting the MTU on the tunnel interface to account for the GRE overhead so routers do not have to fragment the packets. Keep in mind that GRE adds extra 24 bytes of overhead (4 byte GRE Header + 20 byte IP Header). See below on the packet capture between 192.168.1.1 and 192.168.1.2.
Now let's move on to the configuring basic IPSEC between the routers.
!!--First configure the isakmp policy--!!
R1#conf t
R1(config)#crypto isakmp policy 10
R1(config-isakmp)# encr 3des
R1(config-isakmp)# hash md5
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 5
!!--Next let's configure the transform-set (ESP / AH) parameters and the pre-shared key between the routers
R1(config)#crypto isakmp key CISCO address 1.1.1.2
R1(config)#crypto ipsec transform-set AES-128-SHA-1 esp-aes esp-sha-hmac
!!--Source the ipsec connection from gig1.12
R1(cfg-crypto-trans)#crypto map GRE_OVER_IPSEC local-address gig1.12
!!--Create the crypto map, set the peer, attach transform set, and configure the ACL to match traffic that should be IPSEC encapsulated
R1(config)#crypto map GRE_OVER_IPSEC 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)# set peer 1.1.1.2
R1(config-crypto-map)# set transform-set AES-128-SHA-1
R1(config-crypto-map)# match address ipsec-acl
!!--Keep in mind the only traffic we need to IPSEC is GRE traffic between the routers.
!!--This is because all other packets will be encapsulated within GRE.
R1(config-crypto-map)#ip access-list extended ipsec-acl
R1(config-ext-nacl)# permit gre host 1.1.1.1 host 1.1.1.2
Let's configure R2 the same way except change the PEER and mirror the "ipsec-acl".
R2#conf t
R2(config)#crypto isakmp policy 10
R2(config-isakmp)# encr 3des
R2(config-isakmp)# hash md5
R2(config-isakmp)# authentication pre-share
R2(config-isakmp)# group 5
R2(config)#crypto isakmp key CISCO address 1.1.1.1
R2(config)#crypto ipsec transform-set AES-128-SHA-1 esp-aes esp-sha-hmac
R2(cfg-crypto-trans)#crypto map GRE_OVER_IPSEC local-address gig1.12
R2(config)#crypto map GRE_OVER_IPSEC 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R2(config-crypto-map)# set peer 1.1.1.1
R2(config-crypto-map)# set transform-set AES-128-SHA-1
R2(config-crypto-map)# match address ipsec-acl
!!--Make sure that the IPSEC ACLs are exact mirror on both routers.
R1(config-crypto-map)#ip access-list extended ipsec-acl
R1(config-ext-nacl)# permit gre host 1.1.1.2 host 1.1.1.1
Let's do show commands to make sure we have ISAKMP/IPSEC encapsulating and decapsulating packets. I did a few "pings" to get the interesting traffic to flow through the GRE tunnel.
R1#show crypto isa sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
1.1.1.2 1.1.1.1 QM_IDLE 1046 ACTIVE
IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: GigabitEthernet1.12
Crypto map tag: GRE_OVER_IPSEC, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1.1.1.2/255.255.255.255/47/0)
current_peer 1.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 1.1.1.2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1.12
current outbound spi: 0xD3A1D361(3550597985)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xC6C0A240(3334513216)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 3197, flow_id: CSR:1197, sibling_flags FFFFFFFF80004048, crypto map: GRE_OVER_IPSEC
sa timing: remaining key lifetime (k/sec): (4607999/3286)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xD3A1D361(3550597985)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 3198, flow_id: CSR:1198, sibling_flags FFFFFFFF80004048, crypto map: GRE_OVER_IPSEC
sa timing: remaining key lifetime (k/sec): (4607999/3286)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1# show crypto isa policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: Three key triple DES
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 86400 seconds, no volume limit
As you can see the IPSEC between the routers is good to go.
Let's take a look at the IPSEC encapsulated pings between the routers.
As you can see ICMP packets which are encapsulated in GRE is now encapsulated inside IPSEC. So we have [IP]-[IPSEC]-[GRE]-[IP]-[PAYLOAD]-[TRAILER]
Note that you can run the IPSEC in transport mode and get ride of the extra IP header and save a few bytes of overhead.
Running routing is as simple as configuring EIGRP on the interfaces.
R1#conf t
R1(config)#int lo0
R1(config-if)#ip add 10.10.10.1 255.255.255.255
R1(config)#router eigrp 1
R1(config-router)#network 10.10.10.1 0.0.0.0
R1(config-router)#network 192.168.1.0 0.0.0.255
R2#conf t
R2(config)#int lo0
R2(config-if)#ip add 10.10.10.2 255.255.255.255
R2(config)#router eigrp 1
R2(config-router)#network 10.10.10.2 0.0.0.0
R2(config-router)#network 192.168.1.0 0.0.0.255
R1#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(1)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.1.2 Tu0 14 00:01:48 2 1398 0 3
R1#show ip eigrp topology
EIGRP-IPv4 Topology Table for AS(1)/ID(10.10.10.1)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - reply Status, s - sia Status
P 10.10.10.1/32, 1 successors, FD is 128256
via Connected, Loopback0
P 10.10.10.2/32, 1 successors, FD is 27008000
via 192.168.1.2 (27008000/128256), Tunnel0
P 192.168.1.0/24, 1 successors, FD is 26880000
via Connected, Tunnel0
R1#show ip route eigrp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override
Gateway of last resort is not set
10.0.0.0/32 is subnetted, 2 subnets
D 10.10.10.2 [90/27008000] via 192.168.1.2, 00:01:54, Tunnel0
R1#ping 10.10.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/4/5 ms
There you have it ... GRE over IPSEC w/ routing (EIGRP).
Many more articles to come so ....
Please subscribe/comment/+1 if you like my posts as it keeps me motivated to write more and spread the knowledge.

No comments:
Post a Comment