I normally post "How-to articles..." however, I figured this time I'd share a thought that came into my head yesterday as I was watching "Grey's Anatomy". Now I am not particularly a big fan of that show but my wife had a surgery recently and while she was on bed rest, I started to watch the show with her. In one of the episodes, it was revealed that Meredith's mother wrote down all of her research because she was going to get Alzheimer and would eventually forget everything. As I was watching this episode, suddenly a thought popped into my head ... "why do you write how-tos/blogs? ... it's time consuming ... you could be doing something else instead...?" ... As I laid awake mulling over on this thought ... I realized that there are more than one reason as to why I write ...
Wednesday, December 23, 2015
Sunday, December 13, 2015
Configuring LDP - Label Distribution Protocol
In this blogtorial we will go over the basics of LDP, discuss how LDP adjacencies are formed, and also take a look at LDP packets on the wire to gain better understanding of the inner workings of LDP.
LDP stands for Label Distribution Protocol and it is used by routers to share label information about prefixes. For more information regarding LDP check out RFC 5036. At a high glance, LDP first uses UDP hello messages to discover neighbors on the shared segment and then forms a TCP peering with the LDP neighbor to share the label to prefix mapping information. We will see this in detail (packet captures) later in this blogtorial.
Here is a simple topology to follow along.
Monday, December 7, 2015
Configuring DMVPN Phase 3 w/ EIGRP
In this blogtorial we will configure DMVPN Phase 3 and run EIGRP over the tunnel. After reading this blogtorial, I hope that you will have a clear understanding of DMVPN Phase 3 and how it interacts with EIGRP. If you need a primer on DMVPN Phase 1 and Phase 2, please see my DMVPN blogtorials.
Here is the topology.
Here is the topology.
Configuring DMVPN Phase 2 w/ EIGRP
In this blogtorial we will configure DMVPN Phase 2 and configure EIGRP over the DMVPN tunnel. Over the past few blogtorials we've been concentrating on how to configure DMVPN Phase 1 and routing protocols over DMVPN Phase 1. One of the key disadvantage of Phase 1 is that all spoke to spoke traffic must pass through the HUB which is a bit inefficient. DMVPN Phase 2 improves on DMVPN Phase 1 by allowing for on-demand dynamic spoke to spoke tunnels based on traffic patterns.
Here is our topology.
Here is our topology.
Saturday, December 5, 2015
Configuring DMVPN Phase 1 w/ OSPF
In this blogtorial, we will configure DMVPN Phase 1 with OSPF and walk through some gotchas and some pitfalls to be on the look out for.
Due to the hierarchical nature of OSPF and other adjacency intricacies, OSPF is generally discouraged in a DMVPN design.
Due to the hierarchical nature of OSPF and other adjacency intricacies, OSPF is generally discouraged in a DMVPN design.
We are using the same topology as my previous blogtorial "Configuring DMVPN w/ IPSEC and EIGRP", however I'll post the base configs here as well.
Here is our topology.
Configuring DMVPN Phase 1 w/ IPSEC and EIGRP
In this blogtorial we will take a look at how to configure DMVPN, EIGRP over DMVPN and get the traffic going over the DMVPN encrypted using IPSEC. We will break the blogtorial in 3 parts. First we will configure the DMVPN / tunnel and verify end-to-end IP connectivity, then we will move on to configuring routing over the tunnel and finally get IPSEC configured to encrypt everything going over the tunnel.
Here is our topology.
Here is our topology.
Friday, December 4, 2015
Configuring IPSEC VTI (Virtual Tunnel Interfaces)
In this blogtorial, we will briefly explore how to configure IPSEC Virtual Tunnel Interfaces. One of the main advantages of Virtual Tunnel Interfaces is that you do not have to configure an ACL to match all "interesting traffic", thereby minimizing the number of IPSEC security associations (SAs) that must be created.
We'll use the same simple topology from my previous blogtorial "Configuring GRE over IPSEC w/ Routing".
We'll use the same simple topology from my previous blogtorial "Configuring GRE over IPSEC w/ Routing".
Saturday, November 28, 2015
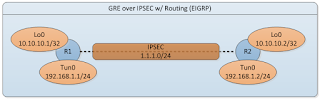
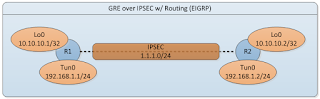
Configuring GRE over IPSEC w/ Routing (EIGRP)
In this blogtorial, we will briefly explore how to configure GRE tunnels over IPSEC with routing (EIGRP). In addition, we will take a closer look down at the packet level on how GRE interacts with IPSEC. Take a look at the simple topology below and let's get started.
Sunday, October 25, 2015
Configuring IPSEC VPN w/ Crypto Maps
In this blogtorial, we will set up a simple preshared key IPSEC VPN tunnel between two routers. We will also use the same topology for my next blogtorial 'Troubleshooting IPSEC VPN'. Lot's of debug and output posted with comments, see below. "Complexity is the enemy of security" therefore we will keep this a simple topology and get started.
Sunday, October 18, 2015
Decoding TimeStamping on Arista 7150
If you need a primer on 'How to configure PTP' on Arista click here. If you understand Arista's implementation of PTP then wait no further and read the rest of the blogtorial on how to decode them from a RAW packet capture.
Key frames DATA is 46bytes and is broken down as follows. What is in bold is important for calculating UTC time of a given packet.
8Bytes - ASIC Ticks
8Bytes - UTC in ns
8Bytes - LAST SYNC
8Bytes - KEY TS
8Bytes - EGRESS Interface DROPS
2Bytes - User defined DEVICE ID
2Bytes - Egress interface of the keyframe
1Byte - FCS TYPE
1Byte - RESERVED
Key frames DATA is 46bytes and is broken down as follows. What is in bold is important for calculating UTC time of a given packet.
8Bytes - ASIC Ticks
8Bytes - UTC in ns
8Bytes - LAST SYNC
8Bytes - KEY TS
8Bytes - EGRESS Interface DROPS
2Bytes - User defined DEVICE ID
2Bytes - Egress interface of the keyframe
1Byte - FCS TYPE
1Byte - RESERVED
Tuesday, May 19, 2015
Configuring BGP - Advertising default route to neighbors - default originate
This post is dedicated to my good friend / colleague Mr. Rage :)
In this blogtorial we will explore one of the methods by which we can advertise a default route to BGP neighbors. One of my colleagues last week asked "would we loose the BGP default route advertisement if the advertising neighbor lost the default route in its own RIB" and honestly I wasn't sure. And I hate being unsure of "something" network related. So I did what any curious person would do, I lab'd it up and it turns out that default route advertisement is not lost when you loose the default route in the routing table, although you can certainly configure it as such.
In this blogtorial we will explore one of the methods by which we can advertise a default route to BGP neighbors. One of my colleagues last week asked "would we loose the BGP default route advertisement if the advertising neighbor lost the default route in its own RIB" and honestly I wasn't sure. And I hate being unsure of "something" network related. So I did what any curious person would do, I lab'd it up and it turns out that default route advertisement is not lost when you loose the default route in the routing table, although you can certainly configure it as such.
Here is a simple topology to get started.
Monday, May 18, 2015
TCP SACK Demystified
In this blogtorial, we will briefly explore TCP SACK (Selective Acknowledgement) option and the benefits of using TCP Selective Acknowledgement. TCP SACK is negotiated in the initial 3-way TCP handshake and both parties must agree to use this option or TCP SACK will not be permitted.
Let's walk through an example and observe what happens when SACK is not enabled.
Let's walk through an example and observe what happens when SACK is not enabled.
Friday, May 1, 2015
BGP Wedgies - Demystified
Usually when we configure BGP we expect the network to converge correctly after all the peerings come up, however under rare circumstances this is not the case. In this blogtorial, we will explore one such corner case scenario in which depending on the order of operation, the BGP topology can end up in a unpredictable topology or a BGP Wedgie.
As usual let's go ahead and get the routers configured and give this topology a wedgie.
Thursday, April 16, 2015
Configuring Cisco - BGP Best External
In this blogtorial, we will briefly explore "BGP Best External" feature and walk through a scenario on how we can achieve sub-millisecond convergence with BGP. This feature is usually used in MPLS environment, although you can pretty much use it anywhere if the design allows it. Here is a simple topology so follow me.
Friday, April 10, 2015
What are TCP Spurious Retransmissions?
First time I saw on "TCP Spurious Retransmissions" on Wireshark, I had to look up the definition of Spurious on Google as I've never heard that word before :). It reads "not being what it purports to be; false or fake". Fake retransmissions? hmmm ... interesting ... started to wonder what this really means. After some investigation, I found out what these mysterious Spurious retransmissions really are. In Wireshark, TCP retransmissions are classified as one of three categories.
Key terms:
RTO - Retransmission Timeout. Every TCP segment as it is sent to the IP layer has a timer associated with it and an ACK should be received before this timer expires. This timer is dynamically adjusted according to RTT and other factors. Here is a good write-up RFC 6298 if you want to get more information on how RTO is calculated.
Key terms:
RTO - Retransmission Timeout. Every TCP segment as it is sent to the IP layer has a timer associated with it and an ACK should be received before this timer expires. This timer is dynamically adjusted according to RTT and other factors. Here is a good write-up RFC 6298 if you want to get more information on how RTO is calculated.
Thursday, April 9, 2015
Troubleshooting eBGP peering
Simple .... BGP topology ... can you get eBGP up and running between R1 and R2?
Objective:
Establish successful and stable eBGP relationship between R1 and R2. With the current start-up config, BGP is IDLE.
Topology diagram and startup config are posted below.
Monday, April 6, 2015
Configuring OSPF - area range vs summary-address
In this blogtorial we are going to take a look at the difference between area range vs summary-address command both of which can be used for OSPF summarization/filtering. Both area range and summary-address commands can also be used for OSPF route filtering. In addition, we will also discuss a few options that are available with area range and summary-address command and pitfalls to be on the lookout for.
Tuesday, March 24, 2015
Configuring OSPF - Summarization Lab
As the CCIE Lab exam requires you to the think outside the box a bit, I will do the same on this lab. Here is a simple topology and the basic start up configuration.
Objectives:
- Summarize 192.168.1.2/32 from Area 2 as 192.168.1.0/24 into area 0.
Restrictions:
- Do not use area-range command or summary-address to summarize the routes into Area 0.
- R3 and other routers in Area 0 or any new additional areas should only have the summary address to reach 192.168.1.2.
- If prefix 192.168.1.2/32 is withdrawn (i.e shutdown loopback0 on R2) from R1 OSPF database then 192.168.1.0/24 should not be summarized/advertised into area 0.
Friday, March 20, 2015
Cisco BUG - PIM join does not make it to CPU
Cisco BUG
CSCue52328 Bug Details
CSCue52328 Bug Details
| PIM joins for some groups not processed at CPU level | |
| Symptom: Under very rare conditions PIM joins from a downstream switch are not forwarded my mcastfwd to PIM to be processed. This has been seen under the following conditions a) Downstream device sending PIM joins is a Arista switch b) There is a local receiver sending IGMP joins for the same group for which PIM joins are received c) Exact trigger is unknown at this point, could be the remote receivers (which result in PIM joins) flapping | |
Thursday, March 12, 2015
Precision Time Protocol PTP - Demystified
As Network Engineers we build highways (maybe Bundesautobahn where there are no speed limits) on top of which various protocols travel. As designers/architects, perhaps it would be beneficial for us to understand what is traveling on the highways we build.
I started to dip my feet into PTP and I realized there is more to PTP than meets the eye. I also realized that I knew very little about its operations so I decided instead of dipping my feet why not just dive right in -- head first. As any curious person would do, I started to read the RFCs and white papers. But before we get into PTP's operation, let's define a handful of key terms.
I started to dip my feet into PTP and I realized there is more to PTP than meets the eye. I also realized that I knew very little about its operations so I decided instead of dipping my feet why not just dive right in -- head first. As any curious person would do, I started to read the RFCs and white papers. But before we get into PTP's operation, let's define a handful of key terms.
Tuesday, February 10, 2015
40G MORE is NOT always BETTER - Why 40G can potentially delay your packets?
40G might actually delay your packets and here is the reason why.
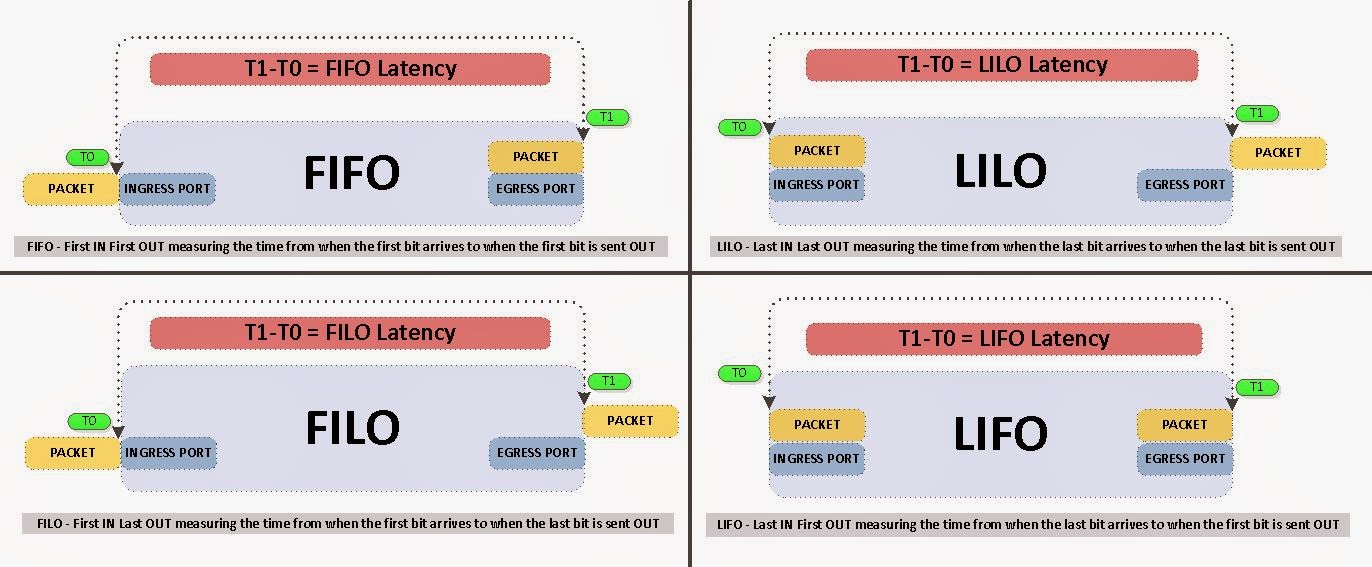
Before we get too much into the semantics behind this, let define some key terms in latency measurements. I am also going to leave out the minor benefits gained from "inter-frame gap" of 40G packets. If you are interested in further information regarding latency testing/benchmarking standards please see RFC 2544.
Monday, February 2, 2015
Troubleshooting OSPF - LAB 1
Here is a quick lab I put together to really test your knowledge about OSPF Path selection and some of the hidden rules behind the path selection.
Simple topology below.
Objective:
Simple topology below.
Objective:
- R3 should choose R2 over Gi1.23 to reach R1 loopback 150.1.1.1/32. Imagine that this is a 40Gbit link where as Gi1.13 is just a 100Mb link. Currently R3 is choosing Gi1.13 to reach R1 loopback 150.1.1.1/32.
- Do not configure any new routing protocols.
- Do not change Area numbers.
- Do not create any NEW areas.
- Do not change OSPF cost values
- R3 should choose R1 with OSPF as the routing protocol so no STATIC routes etc.
Configuration excerpts below so you can configure it in your lab.
Friday, January 9, 2015
EIGRP - Troubleshooting LAB 1
Objective:
- When Gig2 is shutdown on R1, metric for the route to reach Loopback1 should not change on R2.
Subscribe to:
Posts (Atom)